Incorrect permission entries assigned for a user account can prevent programs from accessing the file or folder. Or it may cause unauthorized users to have full access to the objects. In some cases, there may be a reference to obsolete user accounts (or SIDs) in the ACL (permissions list) that you want to clean up.
Have you modified the NTFS permissions for a file or folder wrongly, and want to revert to default (inherited ACLs)?
This article tells you how to replace the file or folder permissions with default inherited permissions quickly using the icacls.exe command-line. The information applies to all versions of Windows, from Windows Vista through Windows 10.
Reset NTFS Permissions for a File or Folder
Using the built-in icacls.exe console tool, you can quickly reset the NTFS permissions for a file or folder. This tool also has a feature where you can reset the permissions for files in a folder and sub-folders, recursively.
- The
icacls.exe /resetcommand-line replaces ACLs (list of permissions) with default inherited ACLs for all matching files or folders.
Important: Your user account needs full control permissions in order to reset or change the permissions of a file or folder. Lack of permissions would cause the error Failed processing n files when running the reset command. If that happens, make sure you first take ownership and assign full control permissions for your account.
Let’s say you have the following permissions for a folder:
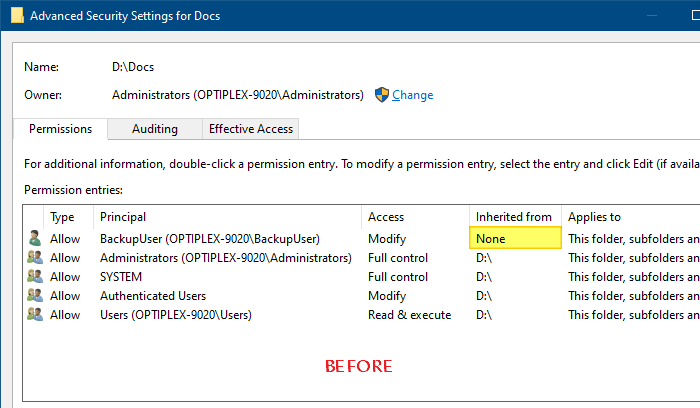
In the above image, you can see that there is a custom (non-inherited) permission entry for the user named BackupUser, for the D:\Docs folder.
- To remove the unwanted permission entries, you can do so via the Advanced Security Settings dialog. But this can be tedious if you want to reset the permissions en masse for all files in a folder and subfolders. That’s where the built-in
icacls.exetool comes to the rescue.
Running the icacls.exe d:\docs command-line to view the folder permissions shows this:
OPTIPLEX-9020\BackupUser:(OI)(CI)(M) BUILTIN\Administrators:(I)(F) BUILTIN\Administrators:(I)(OI)(CI)(IO)(F) NT AUTHORITY\SYSTEM:(I)(F) NT AUTHORITY\SYSTEM:(I)(OI)(CI)(IO)(F) NT AUTHORITY\Authenticated Users:(I)(M) NT AUTHORITY\Authenticated Users:(I)(OI)(CI)(IO)(M) BUILTIN\Users:(I)(RX) BUILTIN\Users:(I)(OI)(CI)(IO)(GR,GE)
- The
(I)entries denote that the permissions are inherited from the parent container. In the above ACL listing, there is only one non-inherited ACL entry forBackupUser.
Reset NTFS permissions for a file or folder
Use this command-line (from admin Command Prompt) syntax to reset the permissions for a file or folder.
icacls file_or_folder_name /reset
To reset the Docs folder permissions, I’d run:
icacls d:\docs /reset
To reset an individual file’s permissions, I’d run:
icacls d:\docs\places.docx /reset
To reset permissions for all files in a folder (e.g., D:\Docs), run:
icacls d:\docs\* /reset
Reset NTFS permissions for a folder, its subfolders, and files
To reset the permissions for the Docs folder along with its sub-folder, and all the files recursively, run this command:
icacls d:\docs /reset /t /c
Related command-line arguments:
/t– Performs the operation on all specified files in the current directory and its subdirectories./c– Continues the operation despite any file errors. Error messages will still be displayed./q– Suppresses success messages./l– Performs the operation on a symbolic link instead of its destination.
You’ll see an output like this:
processed file: d:\docs processed file: d:\docs\Expenses.xlsx processed file: d:\docs\Places.docx Successfully processed 3 files; Failed processing 0 files
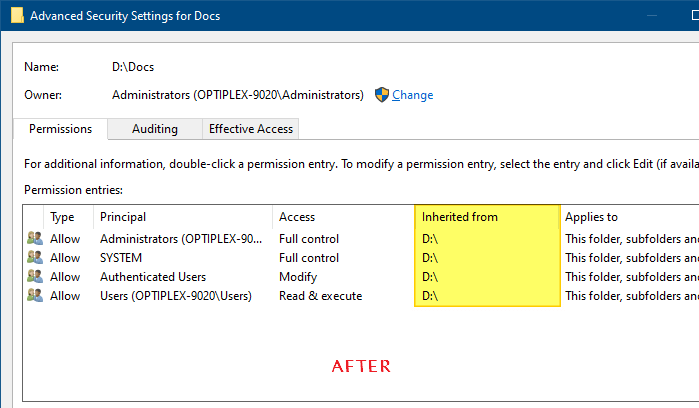
The permissions for the Docs folder is now reset. This means the additional ACL entries will be gone. Only the inherited entries remain. If you had disabled inheritance earlier, the icacls.exe /reset command-line would restore the inherited permissions back.
One small request: If you liked this post, please share this?
One "tiny" share from you would seriously help a lot with the growth of this blog. Some great suggestions:- Pin it!
- Share it to your favorite blog + Facebook, Reddit
- Tweet it!