In Windows 10 Creators Update preview build 15007, Microsoft seems to have fixed the UAC bypass method involving eventvwr.exe. First, how does this bypass work?
When you’re logged in as administrator, Windows binaries that have the execution level set to “highestavailable” and “autoelevate” property set to “true” in the manifest, automatically start elevated without showing the User Account Control prompt.
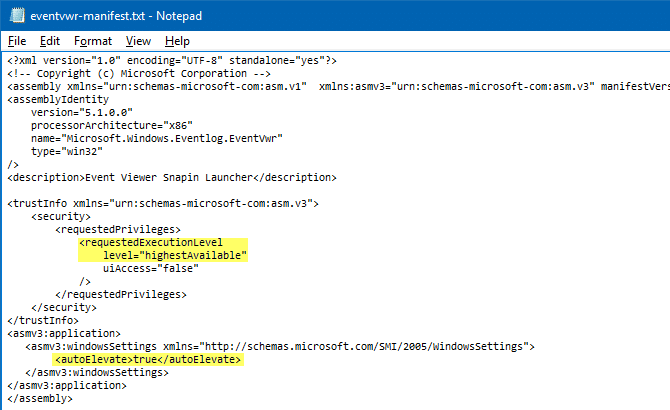
Task Manager (Taskmgr.exe) and Eventvwr.exe are two such examples. Have you noticed that the Task Manager runs elevated by default, but shows no UAC prompt when you’re logged in as administrator?
Security researcher Matt Nelson (@enigma0x3 on Twitter) wrote about a UAC bypass or exploit that uses eventvwr.exe. Eventvwr.exe is essentially a launcher program that executes %systemroot%\system32\eventvwr.msc using ShellExecute method.
What that (ShellExecute) means is that the system uses .MSC file association information to launch the appropriate executable that opens MSC files. Since the parent program eventvwr.exe runs elevated by default, the child process runs elevated as well.
UAC bypass using registry hack
When eventvwr.exe (shell)executes eventvwr.msc file, Windows, rather than using file association info under HKEY_LOCAL_MACHINE\Software\Classes\mscfile, queries the branch here:
HKEY_CLASSES_ROOT\mscfile
FYI, HKEY_CLASSES_ROOT is just a merged view that contains keys, subkeys and values from these two locations:
HKEY_CURRENT_USER\Software\Classes HKEY_LOCAL_MACHINE\Software\Classes
And if identical keys and values exist under both, the ones under HKEY_CURRENT_USER take precedence. So, you can hijack HKEY_CLASSES_ROOT\mscfile by creating the following key:
HKEY_CURRENT_USER\Software\Classes\mscfile\shell\open\command
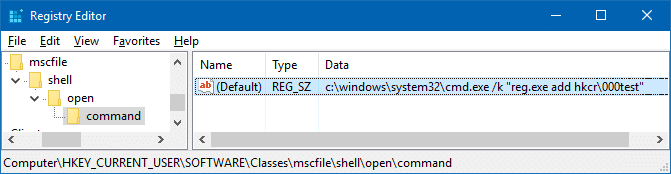
A malicious program or script can set the (default) value data accordingly, so that a PowerShell command/script can be executed with full administrative privileges / high integrity, without even the user knowing.
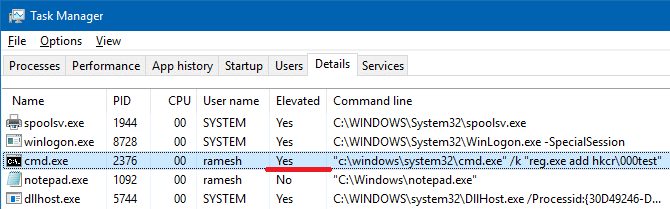
Thus, by hijacking HKEY_CLASSES_ROOT, eventvwr.exe can be effectively used as a launcher program to execute any program arbitrarily — even download ransomware payload from a remote server and run it using PowerShell.exe, under admin privileges.
This is a very effective UAC bypass method as it requires no dropping of files, DLL injection or anything else. Of course, this UAC exploit works only when you’re logged in as administrator.
This has changed in Creators Update preview build 15007. Thankfully, Microsoft has fixed eventvwr.exe in 15007 — it no longer shellexecutes the MSC file. Instead it creates an MMC.exe process directly — file association is not used.
Thanks to Matt Nelson (@enigma0x3) who discovered this bypass method, and to FireF0X (@hFireF0X) who notified that this issue is resolved in 15007 where eventvwr.exe uses CreateProcess to launch mmc.exe instead of ShellExecute. See also: Microsoft Windows – Fileless UAC Protection Bypass Privilege Escalation
One small request: If you liked this post, please share this?
One "tiny" share from you would seriously help a lot with the growth of this blog. Some great suggestions:- Pin it!
- Share it to your favorite blog + Facebook, Reddit
- Tweet it!
Wait a second. I thought the old Windows file association system no longer worked in Windows 10. i.e., I thought if someone tried to pull this trick, he or she would only succeed in bringing up a dialog box that asks the user whether he or she wants to change the app that opens .msc files. How is that not happening?
@Fleet Command: Good question. In Windows 10, setting associations under HKCR (or HKCU…\Classes or HKLM\….classes) hasn’t changed. What has really changed is the Fileexts\…UserChoice. This setting can only be modified using “Open with” or “Default Apps”. If FileExts\.msc\UserChoice exists (but it doesn’t by default), Windows would be executing that app instead when eventvwr.exe is launched.
This would be the order followed:
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.msc\UserChoice [value named “ProgID”]
HKCU\SOFTWARE\Classes\mscfile\shell\open\command
HKLM\SOFTWARE\Classes\mscfile\shell\open\command