Since July last week, Windows Defender started issuing Win32/HostsFileHijack “potentially unwanted behavior” alerts if you had blocked Microsoft’s Telemetry servers using the HOSTS file.
Out of the SettingsModifier:Win32/HostsFileHijack cases reported online, the earliest one was reported at the Microsoft Answers forums where the user stated:
I’m getting a serious “potentially unwanted” message. I have the current Windows 10 2004 (1904.388) and only Defender as permanent protection.
How is that to evaluate, since nothing has changed at my hosts, I know that. Or is this a false positive message? A second check with AdwCleaner or Malwarebytes or SUPERAntiSpyware shows no infection.
“HostsFileHijack” alert if Telemetry is blocked
After inspecting the HOSTS file from that system, it was observed that the user had added Microsoft Telemetry servers to the HOSTS file and routed it to 0.0.0.0 (known as “null-routing”) to block those addresses. Here is the list of telemetry addresses null-routed by that user.
0.0.0.0 alpha.telemetry.microsoft.com 0.0.0.0 alpha.telemetry.microsoft.com 0.0.0.0 asimov-win.settings.data.microsoft.com.akadns.net 0.0.0.0 candycrushsoda.king.com 0.0.0.0 ceuswatcab01.blob.core.windows.net 0.0.0.0 ceuswatcab02.blob.core.windows.net 0.0.0.0 choice.microsoft.com 0.0.0.0 choice.microsoft.com.nsatc.net 0.0.0.0 co4.telecommand.telemetry.microsoft.com 0.0.0.0 cs11.wpc.v0cdn.net 0.0.0.0 cs1137.wpc.gammacdn.net 0.0.0.0 cy2.settings.data.microsoft.com.akadns.net 0.0.0.0 cy2.vortex.data.microsoft.com.akadns.net 0.0.0.0 db5.settings-win.data.microsoft.com.akadns.net 0.0.0.0 db5.vortex.data.microsoft.com.akadns.net 0.0.0.0 db5-eap.settings-win.data.microsoft.com.akadns.net 0.0.0.0 df.telemetry.microsoft.com 0.0.0.0 diagnostics.support.microsoft.com 0.0.0.0 eaus2watcab01.blob.core.windows.net 0.0.0.0 eaus2watcab02.blob.core.windows.net 0.0.0.0 eu.vortex-win.data.microsoft.com 0.0.0.0 eu.vortex-win.data.microsoft.com 0.0.0.0 feedback.microsoft-hohm.com 0.0.0.0 feedback.search.microsoft.com 0.0.0.0 feedback.windows.com 0.0.0.0 geo.settings-win.data.microsoft.com.akadns.net 0.0.0.0 geo.vortex.data.microsoft.com.akadns.net 0.0.0.0 modern.watson.data.microsoft.com 0.0.0.0 modern.watson.data.microsoft.com.akadns.net 0.0.0.0 oca.telemetry.microsoft.com 0.0.0.0 oca.telemetry.microsoft.com 0.0.0.0 oca.telemetry.microsoft.com.nsatc.net 0.0.0.0 onecollector.cloudapp.aria.akadns.net 0.0.0.0 onesettings-bn2.metron.live.com.nsatc.net 0.0.0.0 onesettings-cy2.metron.live.com.nsatc.net 0.0.0.0 onesettings-db5.metron.live.com.nsatc.net 0.0.0.0 onesettings-hk2.metron.live.com.nsatc.net 0.0.0.0 reports.wes.df.telemetry.microsoft.com 0.0.0.0 self.events.data.microsoft.com 0.0.0.0 settings.data.microsoft.com 0.0.0.0 services.wes.df.telemetry.microsoft.com 0.0.0.0 settings.data.glbdns2.microsoft.com 0.0.0.0 settings-sandbox.data.microsoft.com 0.0.0.0 settings-win.data.microsoft.com 0.0.0.0 sqm.df.telemetry.microsoft.com 0.0.0.0 sqm.telemetry.microsoft.com 0.0.0.0 sqm.telemetry.microsoft.com.nsatc.net 0.0.0.0 statsfe1.ws.microsoft.com 0.0.0.0 statsfe2.update.microsoft.com.akadns.net 0.0.0.0 statsfe2.ws.microsoft.com 0.0.0.0 survey.watson.microsoft.com 0.0.0.0 tele.trafficmanager.net 0.0.0.0 telecommand.telemetry.microsoft.com 0.0.0.0 telecommand.telemetry.microsoft.com.nsatc.net 0.0.0.0 telecommand.telemetry.microsoft.com.nsatc.net 0.0.0.0 telemetry.appex.bing.net 0.0.0.0 telemetry.microsoft.com 0.0.0.0 telemetry.remoteapp.windowsazure.com 0.0.0.0 telemetry.urs.microsoft.com 0.0.0.0 tsfe.trafficshaping.dsp.mp.microsoft.com 0.0.0.0 us.vortex-win.data.microsoft.com 0.0.0.0 us.vortex-win.data.microsoft.com 0.0.0.0 v10.events.data.microsoft.com 0.0.0.0 v10.vortex-win.data.microsoft.com 0.0.0.0 v10.vortex-win.data.microsoft.com 0.0.0.0 v10-win.vortex.data.microsoft.com.akadns.net 0.0.0.0 v10-win.vortex.data.microsoft.com.akadns.net 0.0.0.0 v10.vortex-win.data.metron.live.com.nsatc.net 0.0.0.0 v10c.events.data.microsoft.com 0.0.0.0 v10c.vortex-win.data.microsoft.com 0.0.0.0 v20.events.data.microsoft.com 0.0.0.0 v20.vortex-win.data.microsoft.com 0.0.0.0 vortex.data.glbdns2.microsoft.com 0.0.0.0 vortex.data.microsoft.com 0.0.0.0 vortex.data.metron.live.com.nsatc.net 0.0.0.0 vortex-bn2.metron.live.com.nsatc.net 0.0.0.0 vortex-cy2.metron.live.com.nsatc.net 0.0.0.0 vortex-db5.metron.live.com.nsatc.net 0.0.0.0 vortex-hk2.metron.live.com.nsatc.net 0.0.0.0 vortex-sandbox.data.microsoft.com 0.0.0.0 vortex-win-sandbox.data.microsoft.com 0.0.0.0 vortex-win.data.microsoft.com 0.0.0.0 vortex-win.data.metron.live.com.nsatc.net 0.0.0.0 watson.live.com 0.0.0.0 watson.microsoft.com 0.0.0.0 watson.ppe.telemetry.microsoft.com 0.0.0.0 watson.telemetry.microsoft.com 0.0.0.0 watson.telemetry.microsoft.com.nsatc.net 0.0.0.0 wes.df.telemetry.microsoft.com 0.0.0.0 weus2watcab01.blob.core.windows.net 0.0.0.0 weus2watcab02.blob.core.windows.net
And the expert Rob Koch responded saying:
Since you’re null routing Microsoft.com and other reputable websites into a black hole, Microsoft would obviously see this as potentially unwanted activity, so of course they detect these as PUA (not necessarily malicious, but undesired) activity, related to a Hosts File Hijack.
That you’ve decided it’s something you wish to do is basically irrelevant.
As I clearly explained in my first post, the change to perform the PUA detections was enabled by default with the release of Windows 10 Version 2004, so that’s the entire reason for your sudden issue. Nothing is wrong except that you don’t prefer to operate Windows in the manner that the developer Microsoft intended.
However, since your wish is to retain these unsupported modifications in the Hosts file, despite the fact they’ll clearly break many of the Windows functions those sites are designed to support, you’d likely be better off to revert the PUA detection portion of Windows Defender to disabled as it used to be in previous versions of Windows.
It was Günter Born who blogged about this issue first. Check out his excellent post Defender flags Windows Hosts file as malicious and his subsequent post on this topic. Günter was also the first to write about the Windows Defender/CCleaner PUP detection.
In his blog, Günter notes this has been happening since July 28, 2020. However, the Microsoft Answers post discussed above, was created on July 23, 2020, though. So, we don’t know which Windows Defender Engine/client version introduced the Win32/HostsFileHijack telemetry block detection exactly.
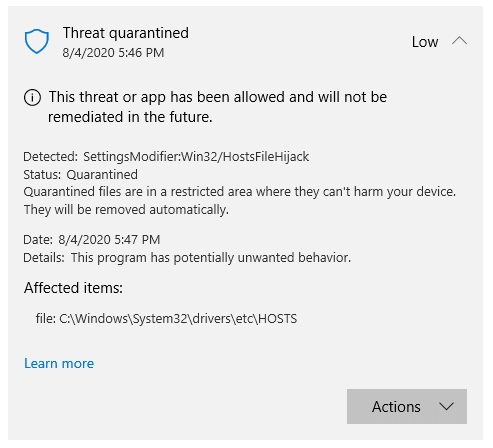
The recent Windows Defender definitions (issued from July 3rd week onwards) consider those ‘tampered’ entries in the HOSTS file as undesirable and warns the user of “potentially unwanted behavior” — with the threat level denoted as “severe”.
Any HOSTS file entry containing a Microsoft domain (e.g. microsoft.com) such as the one below, would trigger an alert:
0.0.0.0 www.microsoft.com (or) 127.0.0.1 www.microsoft.com
Windows Defender would then provide three options to the user:
- Remove
- Quarantine
- Allow on device.
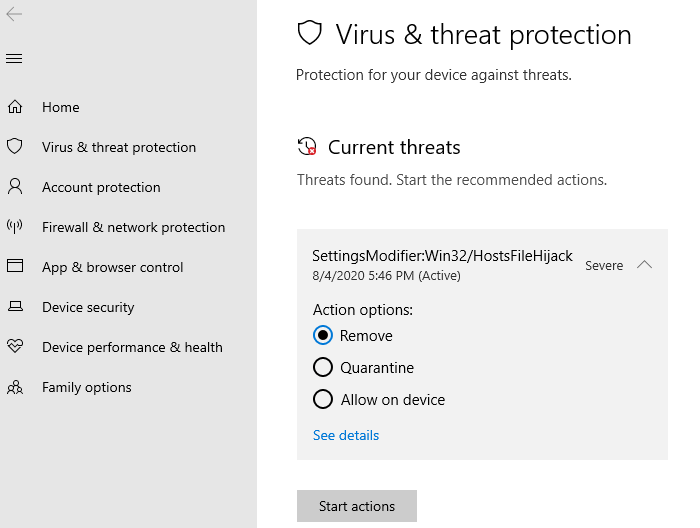
Selecting Remove would reset the HOSTS file to the Windows-default settings, thereby completely erasing your custom entries if any.
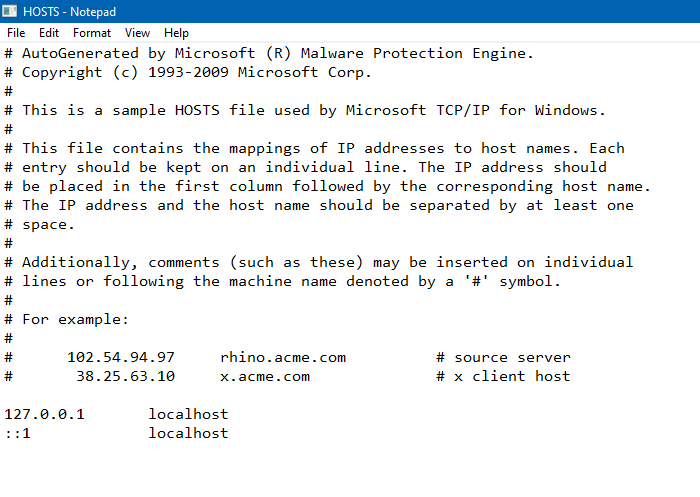
So, how do I block Microsoft’s telemetry servers?
If the Windows Defender team wants to continue with the above detection logic, you have three options to block telemetry without getting alerts from Windows Defender.
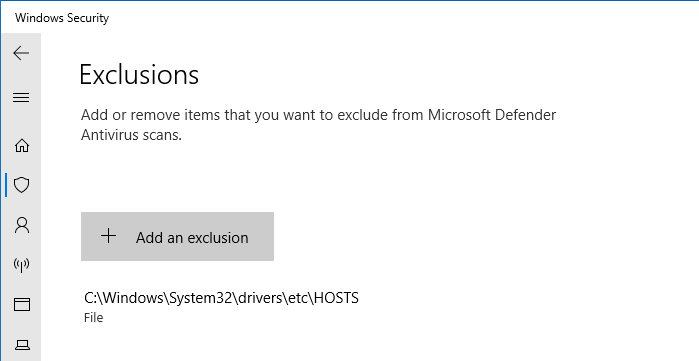
Option 1: Add HOSTS file to Windows Defender exclusions
You can tell Windows Defender to ignore the HOSTS file by adding it to exclusions.
- Open Windows Defender Security settings, click Virus & threat protection.
- Under Virus & threat protection settings, click Manage settings.
- Scroll down and click Add or remove exclusions
- Click Add an exclusion, and click File.
- Select the file
C:\Windows\System32\drivers\etc\HOSTSand add it.
Note: Adding HOSTS to the exclusions list means that if a malware tampers with your HOSTS file in the future, Windows Defender would sit still and do nothing about the HOSTS file. Windows Defender exclusions must be used cautiously.
Option 2: Disable PUA/PUP scanning by Windows Defender
PUA/PUP (potentially unwanted application/program) is a program that contains adware, installs toolbars, or has unclear motives. In the versions earlier than Windows 10 2004, Windows Defender didn’t scan PUA or PUPs by default. PUA/PUP detection was an opt-in feature that needed to be enabled using PowerShell or the Registry Editor.
![]() The
The Win32/HostsFileHijack threat raised by Windows Defender comes under PUA/PUP category. That means, by disabling PUA/PUP scanning option, you can bypass the Win32/HostsFileHijack file warning despite having telemetry entries in the HOSTS file.
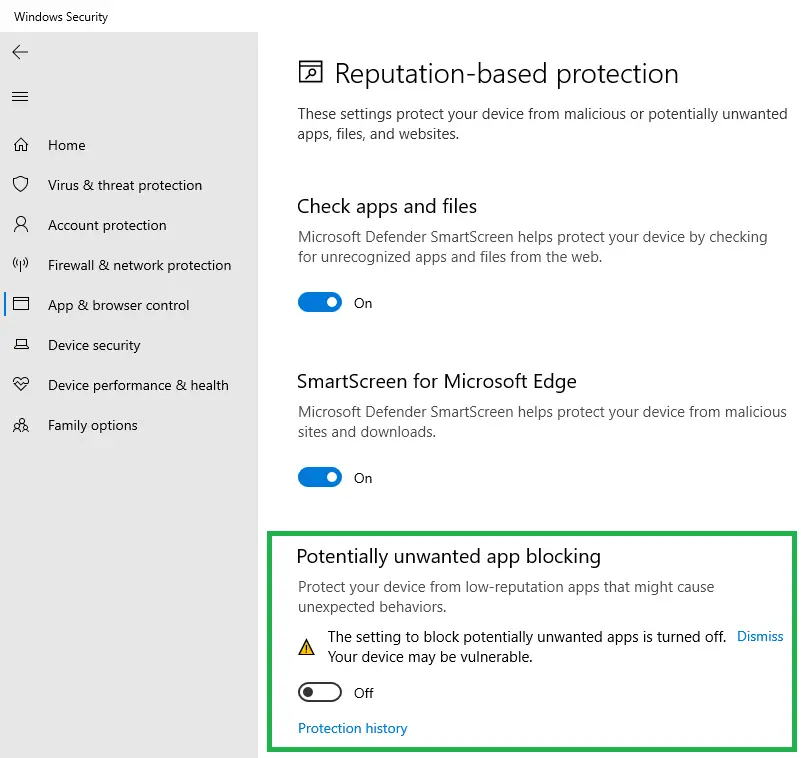
Note: A downside of disabling PUA/PUP is that Windows Defender would do nothing about the adware-bundled setup/installers that you inadvertently download.
![]() Tip: You can have Malwarebytes Premium (which includes real-time scanning) running alongside Windows Defender. That way, Malwarebytes can take care of the PUA/PUP stuff.
Tip: You can have Malwarebytes Premium (which includes real-time scanning) running alongside Windows Defender. That way, Malwarebytes can take care of the PUA/PUP stuff.
Option 3: Use a custom DNS server like Pi-hole or pfSense firewall
Tech-savvy users can set up a Pi-Hole DNS server system and block adware and Microsoft telemetry domains. DNS-level blocking usually requires separate hardware (like Raspberry Pi or a low-cost computer) or a third-party service like OpenDNS family filter. OpenDNS family filter account provides a free option to filter adware and block custom domains.
Alternately, a hardware firewall like pfSense (along with the pfBlockerNG package) can accomplish this easily. Filtering servers at the DNS or firewall level is very effective. Here are some links which tell you how to block the telemetry servers using pfSense firewall:
Blocking Microsoft Traffic In PFSense | Adobo Syntax:
https://adobosyntax.wordpress.com/2019/04/06/blocking-microsoft-traffic-in-pfsense/
How to block in Windows10 Telemetry with pfsense | Netgate Forum:
https://forum.netgate.com/topic/87904/how-to-block-in-windows10-telemetry-with-pfsense
Block Windows 10 From Tracking You:
http://www.weatherimagery.com/blog/block-windows-10-telemetry-phone-home/
Windows 10 Telemetry is bypassing VPN connection : VPN:
Comment
by u/Tzunamii from discussion Windows 10 Telemetry is bypassing VPN connection
in VPN
Connection endpoints for Windows 10 Enterprise, version 2004 - Windows Privacy | Microsoft Docs:
https://docs.microsoft.com/en-us/windows/privacy/manage-windows-2004-endpoints
Editor’s note: I’ve never blocked telemetry or Microsoft Update servers in my systems. If you’re concerned very much about privacy, you can use one of the above workarounds to have the telemetry servers blocked without getting the Windows Defender alerts.
One small request: If you liked this post, please share this?
One "tiny" share from you would seriously help a lot with the growth of this blog. Some great suggestions:- Pin it!
- Share it to your favorite blog + Facebook, Reddit
- Tweet it!
I’m glad I came across your blog. I’ll bookmark it and so remember to peruse it later.
P.S.
I will not be liking, sharing, and that sort of thing as you request; Only because I refuse to use face book, twitter, or etc. because I don’t “like” them, I get by without them, and I wish only for their demise.