Even when running programs elevated (Administrator), certain registry keys and files are not writable. This may be because the files are owned by TrustedInstaller, and no write access granted for Administrators. In that case, running the program as TrustedInstaller can help fix a locked registry key or clear a file that can’t be accessed anyway.
Methods to run a program as TrustedInstaller:
How to Run Programs as TrustedInstaller
You can launch programs as TrustedInstaller using different tools or methods. Follow one of the tools below that suits you.
AdvancedRun
AdvancedRun from Nirsoft allows you to run a program with different settings that you choose, including – low or high priority, start directory, main window state (Minimized/Maximized), run the program with different user or permissions, Operating system compatibility settings, and environment variables. You can also save the desired settings into a configuration file and then run the program automatically from the command-line with the desired settings.
Using Advanced Run, you also launch a program under SYSTEM, TrustedInstaller, or a different user context.
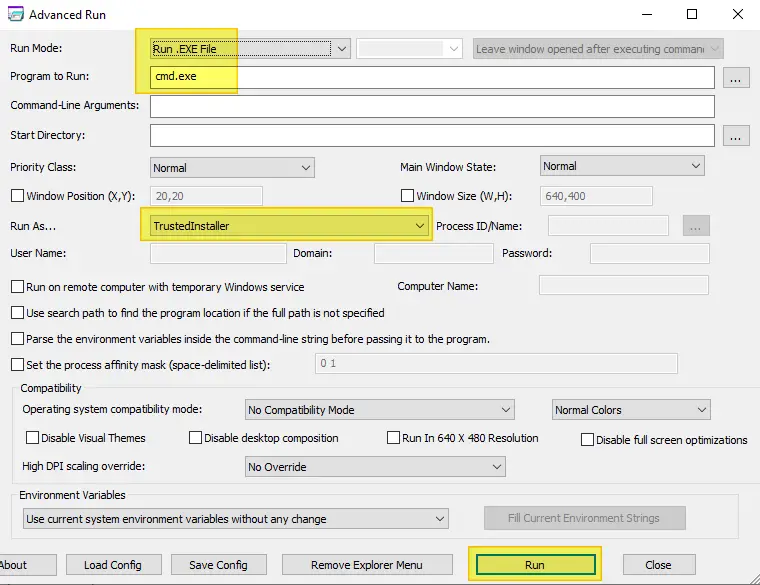
AdvancedRun.exe /EXEFilename "c:\windows\system32\cmd.exe" /RunAs 8 /Run
The above launches Command Prompt as TrustedInstaller.
In the above example, the ‘8’ value of the /RunAs parameter sets the Run As mode to TrustedInstaller. To run a program as SYSTEM user, pass the value ‘4’. If you don’t know what is the right value to use from command-line, simply choose the desired option from the user interface, save it to config file, and then check the values stored in the config (.cfg) file.
PowerRun
PowerRun is a freeware utility that can launch programs under the TrustedInstaller privileges. If you have a locked-down registry key or a file owned by TrustedInstaller and can’t rename or replace the file, this tool can help.
Download PowerRun and run it. Add the necessary program(s) to the list and run as TrustedInstaller.
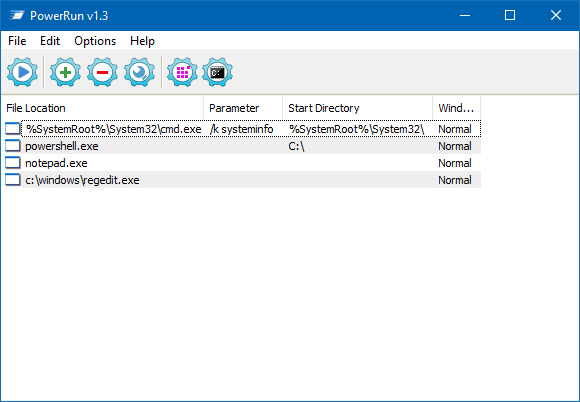
PowerRun command-line support
PowerRun supports the following command-line arguments.
Usage: PowerRun_x64.exe [/SW:<Window State (0-3)] [/WD:<Working Directory>] [<file path> Required!] [<file commands>] Commands: /SW:0 = Hide window /SW:1 = Show window (Default) /SW:2 = Minimize window /SW:3 = Maximize window /WD:(Path) = Working directory /SYS = Only System User (Not TrustedInstaller) Examples: PowerRun_x64.exe "C:\Test.exe" PowerRun_x64.exe "C:\Test.exe" param1 param2 etc. PowerRun_x64.exe "C:\Test.bat" param1 param2 etc. PowerRun_x64.exe /SW:2 "/WD:C:\" notepad.exe C:\test.txt PowerRun_x64.exe Regedit.exe "C:\Test.reg" PowerRun_x64.exe Regedit.exe /S C:\Test.reg PowerRun_x64.exe %SystemRoot%\system32\cmd.exe PowerRun_x64.exe cmd.exe /k echo hello world! PowerRun_x64.exe /SYS cmd.exe /k echo hello world! PowerRun_x64.exe /SW:0 "Reg.exe" add "HKLM\Software\keyname" /v "valuename" /t REG_SZ /d "hello" /f
NSudo
NSudo (GitHub) is a similar tool like PowerRun, but it can launch programs under System (LocalSystem), Current User, Current Process, or the TrustedInstaller account.
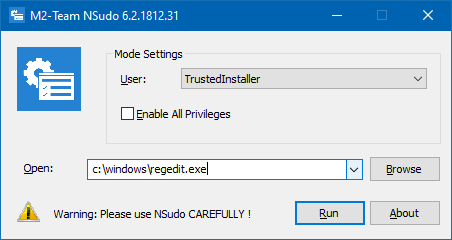
NSudo : Command-line support
NSudo version 6.2.1812.31 -U:[ Option ] Create a process with specified user option. Available options: T TrustedInstaller S System C Current User P Current Process D Current Process (Drop right) PS: This is a mandatory parameter. -P:[ Option ] Create a process with specified privilege option. Available options: E Enable All Privileges D Disable All Privileges PS: If you want to use the default privileges to create a process, please do not include the "-P" parameter. -M:[ Option ] Create a process with specified Integrity Level option. Available options: S System H High M Medium L Low PS: If you want to use the default Integrity Level to create a process, please do not include the "-M" parameter. -Priority:[ Option ] Create a process with specified [rocess priority option. Available options: Idle BelowNormal Normal AboveNormal High RealTime PS: If you want to use the default Process Priority to create a process, please do not include the "-Priority" parameter. -ShowWindowMode:[ Option ] Create a process with a specified window mode option. Available options: Show Hide Maximize Minimize PS: If you want to use the default window mode to create a process, please do not include the "-ShowWindowMode" parameter. -Wait Make NSudo wait for the created process to end before exiting. PS: If you don't want to wait, please do not include the "-Wait" parameter. -CurrentDirectory:[ DirectoryPath ] Set the current directory for the process. PS: If you want to use the NSudo's current directory, please do not include the "-CurrentDirectory" parameter. -UseCurrentConsole Create a process with the current console window. PS: If you want to create a process with the new console window, please do not include the "-UseCurrentConsole" parameter. -Version Show version information of NSudo. -? Show this content. -H Show this content. -Help Show this content. Context Menu: -Install : Copy NSudo to the Windows directory and add the context menu. -Uninstall : Remove NSudo in the Windows directory and the context menu. PS: 1. All NSudo command arguments is case-insensitive. 2. You can use the "/" or "--" override "-" and use the "=" override ":" in the command line parameters. For example, "/U:T" and "-U=T" are equivalent. 3. To ensure the best experience, NSudoC does not support context menu.
Example:
To run Command Prompt as TrustedInstaller, enable all privileges and the default Integrity Level:
NSudo -U:T -P:E cmd
Process Hacker
If you’re using the excellent Process Hacker process manager program, you can launch a program as TrustedInstaller in two different ways:
Option 1: Using built-in options
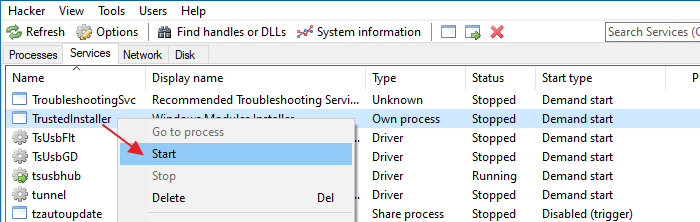
In Process Hacker, click on the Services tab. Right-click the TrustedInstaller service and click Start.
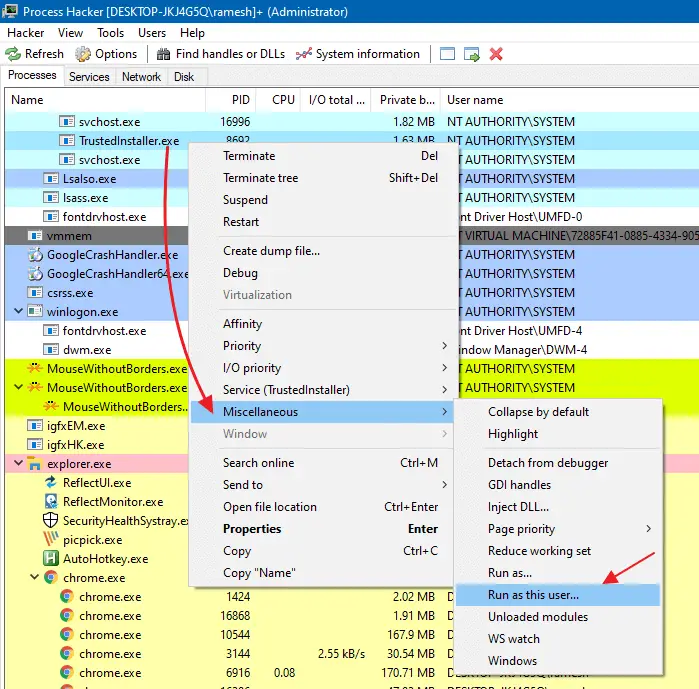
Switch back to the Processes tab, right-click TrustedInstaller.exe, click Miscellaneous and click Run as this user…
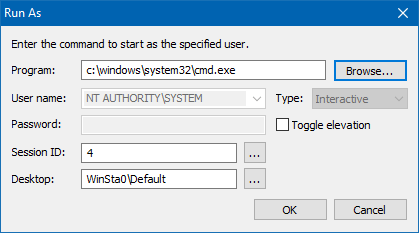
Type the program you want to run as TrustedInstaller — e.g., Command Prompt (cmd.exe), and click OK.
Note that the User name field reads NT AUTHORITY\SYSTEM. Also, when a program is launched under TrustedInstaller context, Task Manager or any process manager would show that it’s running as the SYSTEM user.
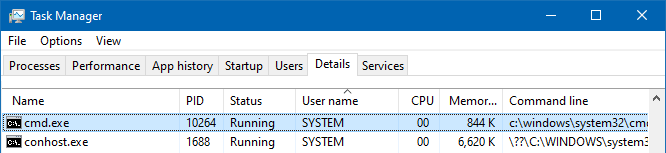
This is the case if you use any method in the above article. It’s normal and can be ignored. The spawned process runs with TrustedInstaller privileges although it says SYSTEM.
Option 2: Using a Plugin
Downloading a Process Hacker plugin (.dll file) lets you run programs as TrustedInstaller via Process Hacker main menu. Here are the Plugin download links:
TrustedInstallerPlugin_x32.zip (for 32-bit) https://wj32.org/processhacker/forums/download/file.php?id=795&sid=37bfe842abb595845e0663ae5b4da06b TrustedInstallerPlugin_x64.zip (for 64-bit) https://wj32.org/processhacker/forums/download/file.php?id=796&sid=37bfe842abb595845e0663ae5b4da06b Source code at GitHub: https://github.com/processhacker/plugins-extra/tree/master/TrustedInstallerPlugin (via) TrustedInstaller - Process Hacker Forums: https://wj32.org/processhacker/forums/viewtopic.php?t=2407
After you copy TrustedInstallerPlugin.dll to the Process Hacker\Plugins directory, close and reopen Process Hacker.
You’ll see the Run as trusted installer… command under the main menu.
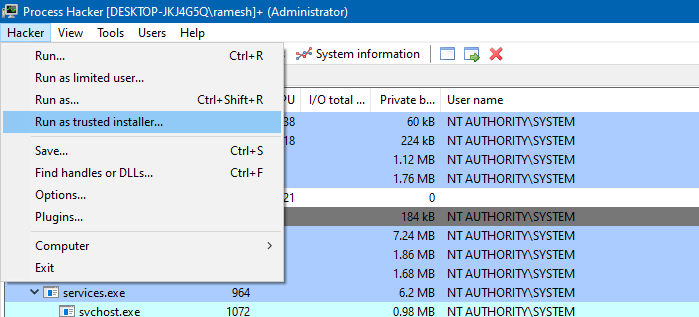
RunX from d7xTech
RunX is a digitally signed executable that can launch any process with a Local System account or TrustedInstaller account privileges. It is also designed to optionally pass command line arguments to that app without having to open an admin Command Prompt window and navigate to the appropriate path first. It can also capture and display the program’s exit code.
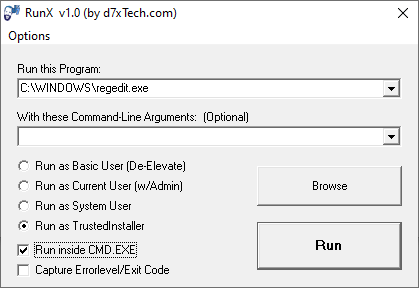
The “Run inside CMD.EXE” option will launch Command Prompt window first and launch the target program from there. That way you use the Command Prompt window to run subsequent commands under TrustedInstaller.
Download RunX and RunXcmd from:
New App: RunX and RunXcmd – d7xTech.com (formerly Foolish IT): https://www.d7xtech.com/new-app-runx-and-runxcmd/
The package also includes a console version of the tool named RunXcmd. It’s designed to do the above but for scripting purposes, when you need your script to wait on the process you are running to terminate, and/or when you or your script needs to know the process exit code via %errorlevel% output.
Here’s the list of command-line switches it supports:
Usage: RunXcmd.exe /exec="[path\file.exe]" /wait /account=[user|system|ti] /args=[] Arguments: /exec="[path\file.exe]" (Required; must be wrapped in quotes.) /wait (Optional, Wait for the app to finish; useful in scripting. RunX also returns the /exec file's exit code as it's own.) /account=[user|system|ti] (Optional, Run as User(Non-Admin), System, or TrustedInstaller. If this switch is not specified, TrustedInstaller is assumed.) /args= (Optional, must be the LAST switch, everything after this is passed to the /exec file. Do NOT wrap args in quotes, unless you intend for the quotes to be passed to the /exec file.) Example: (Run as Standard User with Arguments) RunXcmd.exe /exec="c:\path\file.exe" /account=user /args=/Arg1 /Arg2 /Etc. Example: (Run as Trusted Installer and Wait/Return Exit Code) RunXcmd.exe /exec="c:\path\file.exe" /wait
Closing Words
Running programs under TrustedInstaller privileges can be risky, and you won’t need to do that in most cases, and as long as programs can access the necessary system files. This sort of elevation has to be used only when it’s necessary and if you know what you’re doing.
I’ve seen cases where TrustedInstaller incorrectly locked down specific system DLLs and the system itself couldn’t read the file, showing 0 KB in Explorer. Accessing the file properties and clicking the Security tab showed that the Permissions couldn’t be displayed. And ICACLS.EXE when running from Admin Command Prompt couldn’t even see the file, as it said “The system cannot find the file specified. Successfully processed 0 files; Failed processing 1 files”.
Eventually, I had to use launch Command Prompt under Ti rights and then clear those files before running the System File Checker.
One small request: If you liked this post, please share this?
One "tiny" share from you would seriously help a lot with the growth of this blog. Some great suggestions:- Pin it!
- Share it to your favorite blog + Facebook, Reddit
- Tweet it!
How do I use PowerRun to “run as TrustedInstaller.”? There are no options to “run as TrustedInstaller, and you guide does not show how files can be run with TrustedInstaller??
RunAsTI program is the best way to do it https://github.com/jschicht/RunAsTI